Ransomware Report
You can check the latest ransomware information.
- title
- BuLock ransomware
- Registration date
- 2024-03-18
- views
- 17511
[ BuLock ransomware ]
[Virus/malware activity reported: BuLock ransomware]
Due to a breach believed to be in the form of BuLock ransomware,
we would like to confirm the situation and provide a warning as follows.
BuLock ransomware
The ransomware in question is called BuLock and appears to be changing all files with the file name.extension.bulock72.
How it works
file version
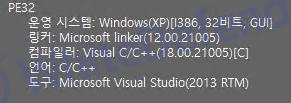
[Figure 1 Ransomware executable file compiler information]
[Figure 2 File information in window properties]
Ransomware operation characteristics
-
It was created based on C++, and the ransomware copies files from the initial execution location to the AppDataLocal folder and executes them. A registry value that executes the copied file in the user account's startup program is also created and encrypted.
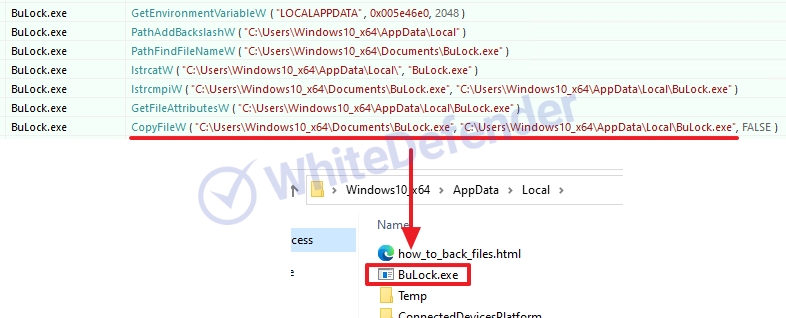
[Figure 3 Dynamic information and created files copying files to the corresponding location]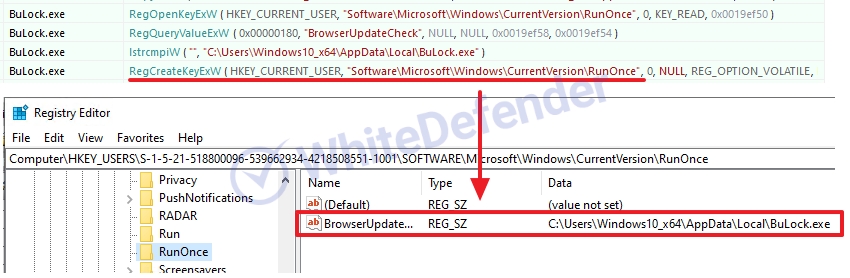
[Figure 4 Dynamic code and generated values that register the ransomware executable file created in the Local folder in the user's startup program registry]
Infection results
The guidance file <how_to_back_files.html> is created in each path, and the files are changed to <file name.extension.bulock72> when encryption is performed.
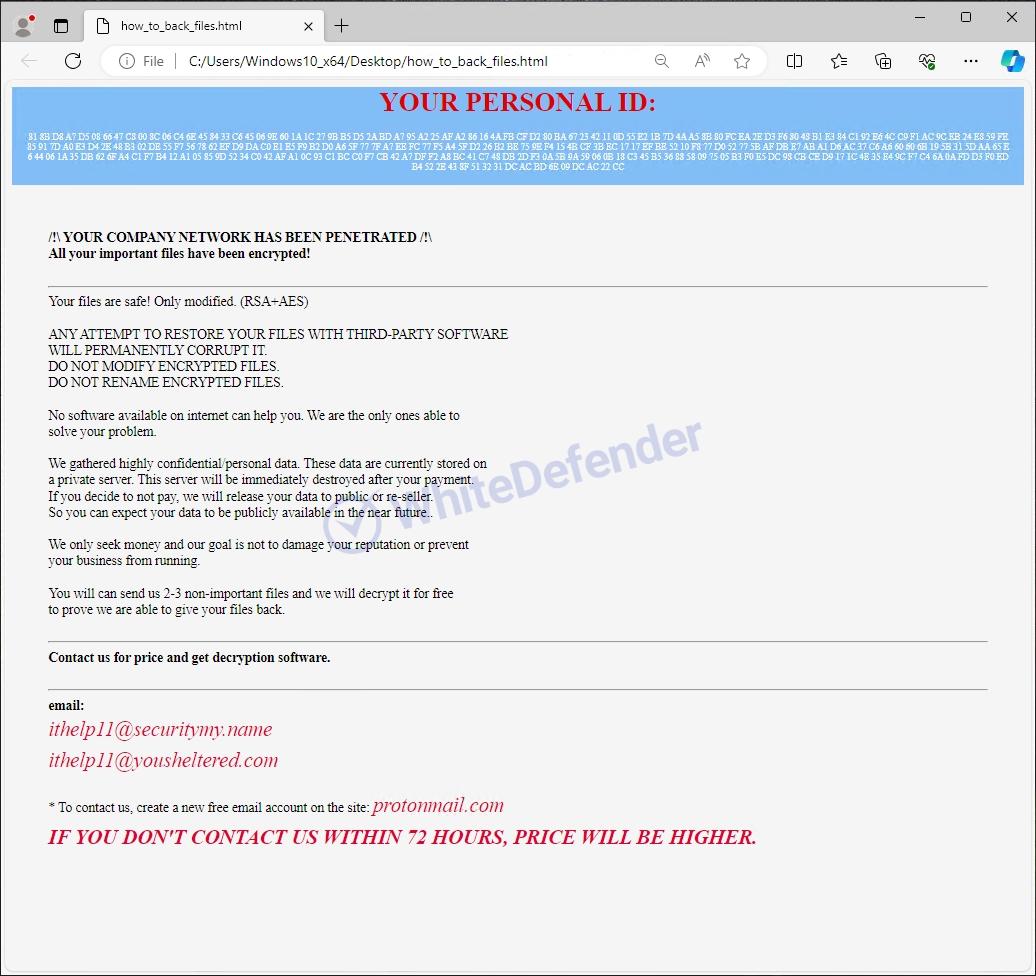
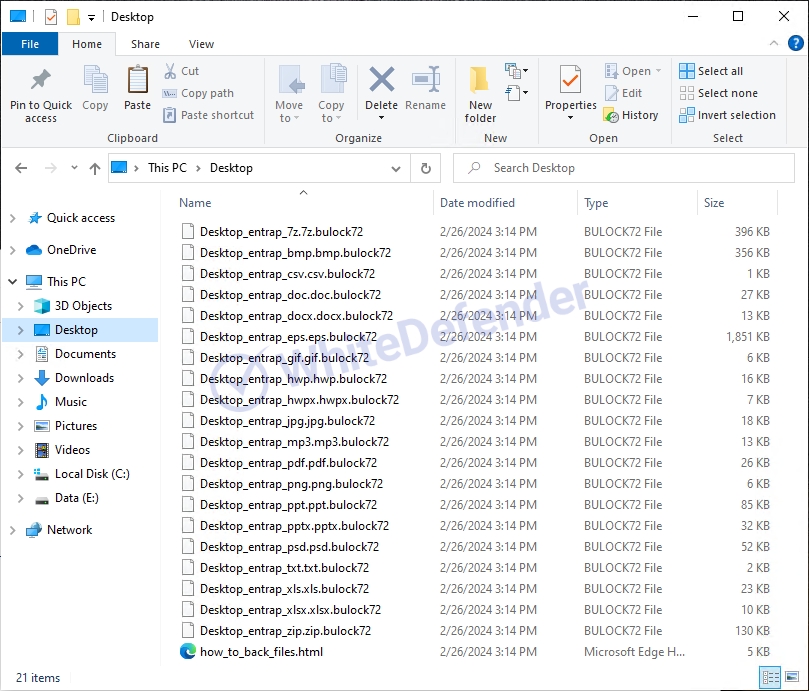
[Figure 5 Infection results]
White Defender compatible
It supports real-time automatic restoration of files that will be encrypted before the malicious actions and blocking of White Defender ransomware.
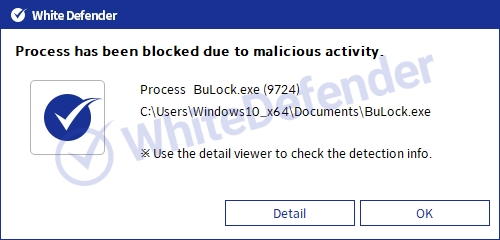
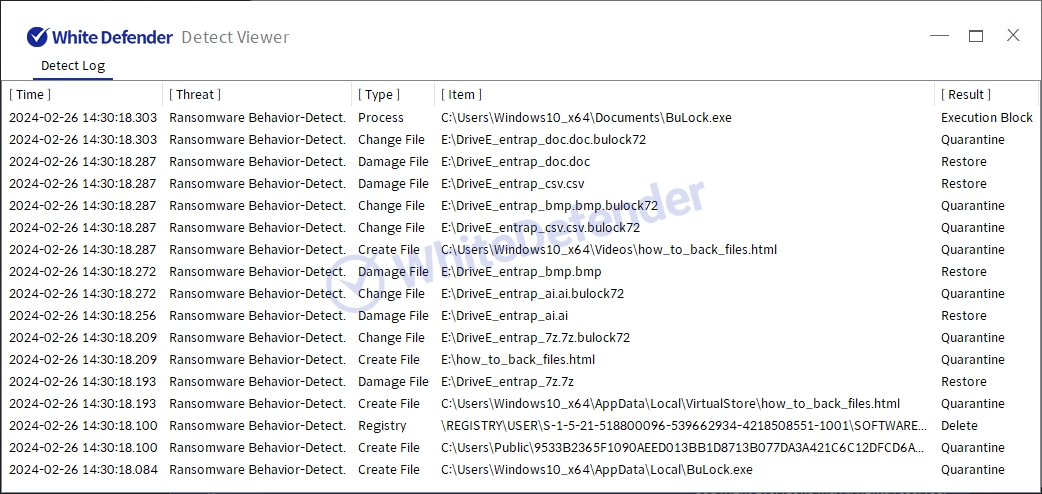
[Figure 6 Block message]

- Previous post
- Slime ransomware
- next post
- ZeroGuard Ransomware

